CypSec Research Reveals „Follow the Noise“ Methodology for Detecting Sophisticated Intrusions Through Honeypot Behavioral Analysis
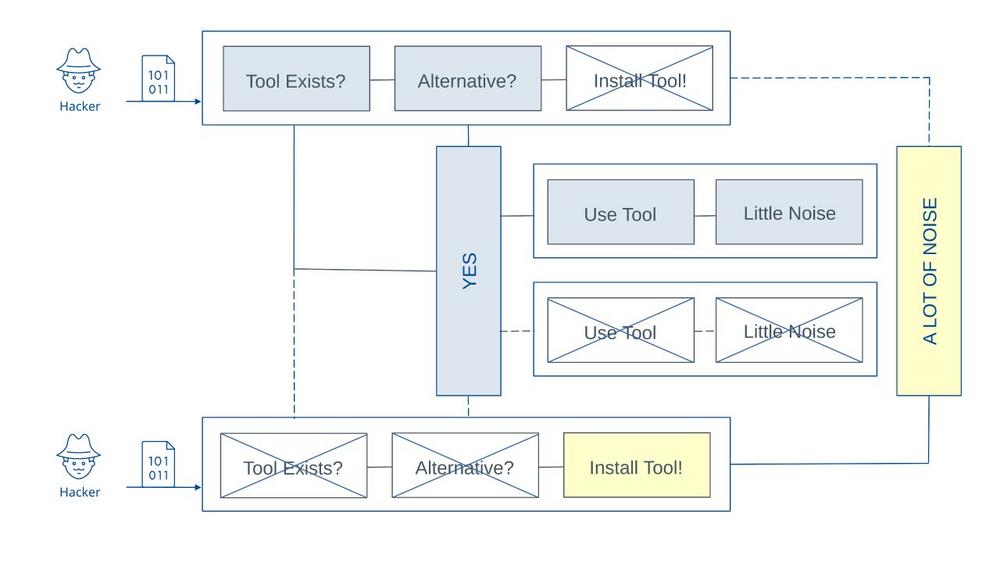
The study analyzes the critical decision points attackers face after gaining initial access to a compromised system. At this juncture, adversaries must choose between three primary operational paths: leveraging existing tools already present on the system, installing specialized hacking utilities, or pivoting to alternative attack methodologies using native system capabilities. Each path generates distinct "noise" profiles in the form of behavioral signatures that sophisticated deception environments can capture, analyze, and weaponize for early detection.
"Sophisticated attackers are trained to minimize their footprint, yet our research proves they cannot operate silently when pursuing objectives," stated Frederick Roth, Chief Information Security Officer at CypSec. "The ‚Follow the Noise‘ methodology transforms this operational constraint into a detection advantage. By understanding the behavioral economics of post-compromise activity, we can identify advanced adversaries before they reach critical assets, not by looking for known malware signatures, but by recognizing the inevitable disturbances their presence creates."
The research maps the fundamental trilemma facing adversaries in compromised environments:
- Native Tool Exploitation: Sophisticated attackers often attempt "living off the land", using legitimate system administration tools (PowerShell, WMI, PsExec, native binaries) for malicious purposes. While this minimizes forensic footprint, it creates behavioral anomalies: unusual process parent-child relationships, atypical command-line arguments, anomalous execution contexts. These deviations from baseline administrative activity generate "semantic noise" that deception environments can flag through behavioral analytics.
- Custom Tool Deployment: When native tools prove insufficient, attackers deploy specialized utilities, such as password extractors, network scanners and privilege escalation exploitation frameworks. This installation activity creates "infrastructure noise": file system modifications, registry changes, service installations, network connections to external repositories. Even fileless techniques leave memory artifacts and API call patterns that sophisticated honeypots capture through kernel-level monitoring and memory forensics.
- Alternative Attack Vectors: Constrained attackers may pivot to unexpected methodologies: abusing legitimate application features, exploiting misconfigured services, or leveraging trust relationships. These alternative paths create "architectural noise", represented by unusual authentication patterns, abnormal data flows, unexpected lateral movement corridors that deviate from predicted network topology.
CypSec’s research demonstrates that honeypot environments function as "controlled acoustic spaces" where this operational noise becomes amplified and analyzable. Unlike production systems, where legitimate activity creates background interference, deception environments maintain pristine baselines where any deviation signals potential adversary presence.
The workflow analysis reveals that sophisticated attackers, those most capable of evading signature-based detection, actually generate the most distinctive noise profiles through their very sophistication. Their preference for custom tools, their systematic enumeration procedures, their cautious but complex operational security measures create extended, multi-stage behavioral signatures that simpler opportunistic attackers do not produce.
"Paradoxically, the more sophisticated the attacker, the more detectable they become in properly instrumented deception environments," noted the CypSec research team. "Their operational discipline requires time, their tool sophistication requires deployment, their caution requires reconnaissance, all of which generate extended interaction patterns with honeypot systems that we can analyze, correlate, and attribute."
The research presents detailed workflow diagrams mapping attacker progression through compromised deception environments:
- Reconnaissance Noise: Upon access, attackers inevitably perform system enumeration, such as identifying processes, network connections, user accounts, defensive tools. Even passive reconnaissance generates detectable patterns: unusual API queries, atypical registry accesses, anomalous network discovery traffic. Honeypot instrumentation captures these preliminary probes, enabling detection before malicious action.
- Tool Selection Noise: The decision point between native and custom tools creates distinctive behavioral branches. Attackers evaluating available utilities generate file system and process inspection patterns. Those retrieving external tools create network connection artifacts. Those improvising with unexpected native functionality generate anomalous command sequences. Each branch produces detectable decision signatures.
- Execution Noise: Actual tool usage, whether native or custom, generates operational signatures: process injection patterns, memory allocation anomalies, network traffic characteristics, authentication attempts. Sophisticated attackers attempting to minimize this noise often inadvertently extend it through complex obfuscation procedures that themselves become detectable.
- Persistence Noise: Establishing continued access requires modifying system state, such as creating services, scheduling tasks, modifying registry keys and establishing backdoors. These persistence mechanisms generate "structural noise" that alters system baseline in detectable ways, even when employing advanced rootkit techniques.
The "Follow the Noise" methodology transitions from academic observation to operational detection through CypSec’s managed deception services. Honeypot deployments are instrumented to capture multi-dimensional behavioral data: kernel-level system calls, memory forensics snapshots, network traffic analysis, and semantic command evaluation.
Machine learning models trained on this behavioral data distinguish between automated scanning, opportunistic intrusion attempts, and sophisticated adversary campaigns. The extended duration of sophisticated attacker interactions, often spanning hours or days as they carefully explore deception environments, provides sufficient data for high-confidence attribution and threat intelligence generation.
The research challenges conventional security architectures that prioritize perimeter prevention over post-compromise detection. "Follow the Noise" demonstrates that determined adversaries will inevitably breach defenses, and that effective security requires instrumented environments where their inevitable operational signatures become detectable.
For enterprise security teams, this implies strategic deployment of deception assets throughout critical network segments, not as isolated honeypots, but as distributed sensor networks that force attackers to generate noise to achieve objectives. For critical infrastructure operators, it suggests operational technology environments instrumented with industrial control system decoys that capture targeted adversary campaigns invisible to conventional monitoring.
CypSec’s research incorporates data from international deception networks, including academic partnerships with institutions researching attacker behavioral economics. The methodology has been validated against real-world intrusion attempts captured in production deception environments, with findings peer-reviewed through threat intelligence community sharing.
The research team emphasizes that "Follow the Noise" complements rather than replaces existing detection methodologies. Signature-based detection, anomaly monitoring, and threat intelligence remain essential, but behavioral analysis of attacker tool selection and alternative path exploration provides additional detection layer specifically targeting sophisticated adversaries optimized for evasion.
CypSec is an international cybersecurity company providing integrated security ecosystem solutions for government, defense, critical infrastructure, and enterprise clients. The company delivers proprietary software platforms and senior practitioner consulting that enable organizations to prevent, detect, and contain advanced attacks without surrendering operational autonomy or budget predictability.
CypSec Group
Suite 801, 5500 North Service Road
CDNL7L 6W6 Burlington, Ontario
Telefon: +31653169442
https://cypsec.de/
Chief Executive Officer
Telefon: +31653169442
E-Mail: daria.fediay@cypsec.de
![]()



